In discussions regarding the cloud, it is sometimes argued that it is more secure to leave your data with US cloud service providers.
The question is – more secure than what?
More secure than a low-priority server rack in the basement? Most likely. A low bar is easy to get over. You can almost sense the cobwebs and water leaks creeping into the mythical server basement.
Fortunately, in most cases the alternatives in reality are different. Both when it comes to running things on-premises, but especially when looking at the choices available on the market for buying cloud services from providers.
Cleura and many other companies offer cloud infrastructure as a service (IaaS) but also platform as a service (PaaS) in competition with Azure, AWS and Google Cloud. Cleura does this from its data centre regions in Sweden and Germany.
Organisations can thus move to the cloud – with hosting by an external service provider – without handing over their data to US cloud service providers.
The alternative: OpenStack-based clouds
We at Cleura, and many with us, use the OpenStack platform to deliver cloud infrastructure. Today, you can get OpenStack-based public cloud services delivered from over 180 data centres worldwide.
OpenStack was created by the US hosting company Rackspace and the US space agency NASA.
In other words, it is technology with American roots.
Rackspace and NASA discovered that they had each built complementary cloud components. They decided to merge the projects and created what can best be described as a replacement for AWS.
Those involved at the time have said that the project could have fallen apart early on. The difficulties seemed insurmountable, and a US senator reportedly even tried to stop the project. The senator feared that automated cloud operations would lead to fewer jobs in the state’s data centres. NASA’s bureaucracy was also an obstacle.
The project ultimately succeeded despite the odds. Those who want to delve deeper can read Wire magazine’s fascinating article The Secret History of OpenStack, the Free Cloud Software That’s Changing Everything.
OpenStack is special because it is based on collaboration – not just between Rackspace and NASA, but between organisations across the world. Because Rackspace and NASA released OpenStack with an open source licence, everyone could contribute improvements.
And no one has to ask anyone for permission to use OpenStack, or pay a licence fee.
Hundreds of organisations using or relying on OpenStack still contribute with code, financial support or through other means. OpenStack can be likened to a commons that its users nurture and care for. The difference with a plot of land is that OpenStack becomes more valuable to everybody as more organisations use it and participate in the community. As a result, OpenStack has become one of the world’s most successful open source projects.
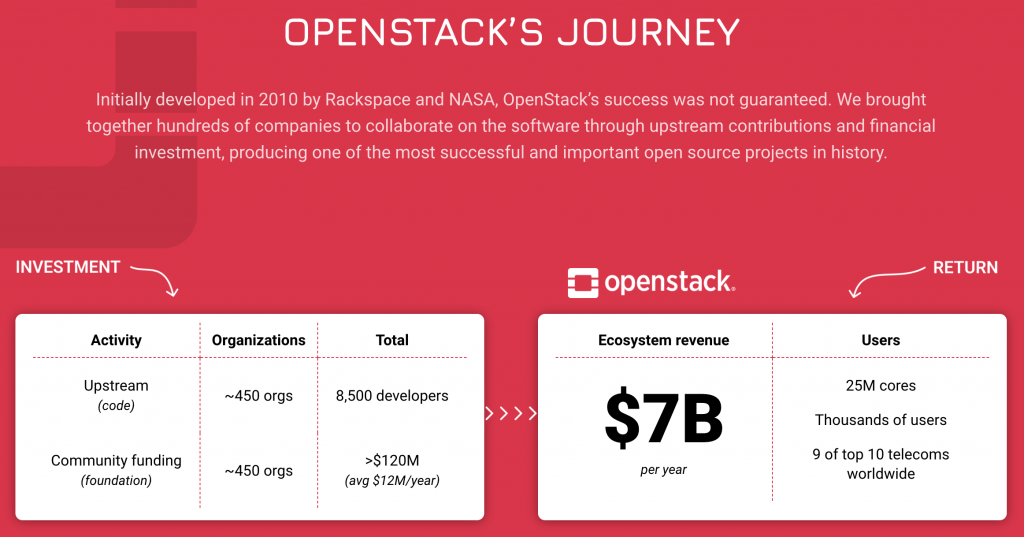
Thanks to OpenStack, European and Swedish cloud service providers like Cleura can offer infrastructure as a service (IaaS) to organisations that need to comply with the GDPR and other regulations. These are pure, scalable cloud services provided from, for example, Cleura’s data centre regions in Sweden and Germany.
The OpenStack project’s home has long been the OpenInfra Foundation. The foundation ensures the project is managed and developed for the benefit of the community, without appeasing any individual company’s special interests.
In addition to OpenStack, the foundation hosts related projects in areas such as AI/machine learning, CI/CD, containers and edge computing. Cleura is a gold member of the OpenInfra Foundation and is represented on the advisory board of OpenInfra Europe.
What about security?
A recurring refrain is that US cloud service providers allocate large amounts of money, or devote a large number of staff, to security. However, this doesn’t say much about the results achieved.
Are staff resources used effectively? Do they have to clean up messes after the fact, due to a fast pace of development leading to security flaws? Are new features added at a pace which increase the attack surface to the detriment of security? Is old technical debt burdening the code, requiring extra effort from a security point of view?
Does the solution have such a large customer base that adversaries see it as a particularly attractive target?
It seems logical that the more people use a standardised cloud solution, and the more sensitive the data processed in that cloud solution, the more attractive it will be for adversaries to search for security vulnerabilities. One vulnerability could then be used against a larger number, or more sensitive, targets. It is only natural that a provider of such a solution has to allocate more resources to security.
In addition, a disruption at the provider may affect many organisations at the same time.
It is worth mentioning here that Google has identified the dominance of one of its competitors as a particularly big security problem, not least for the public sector.
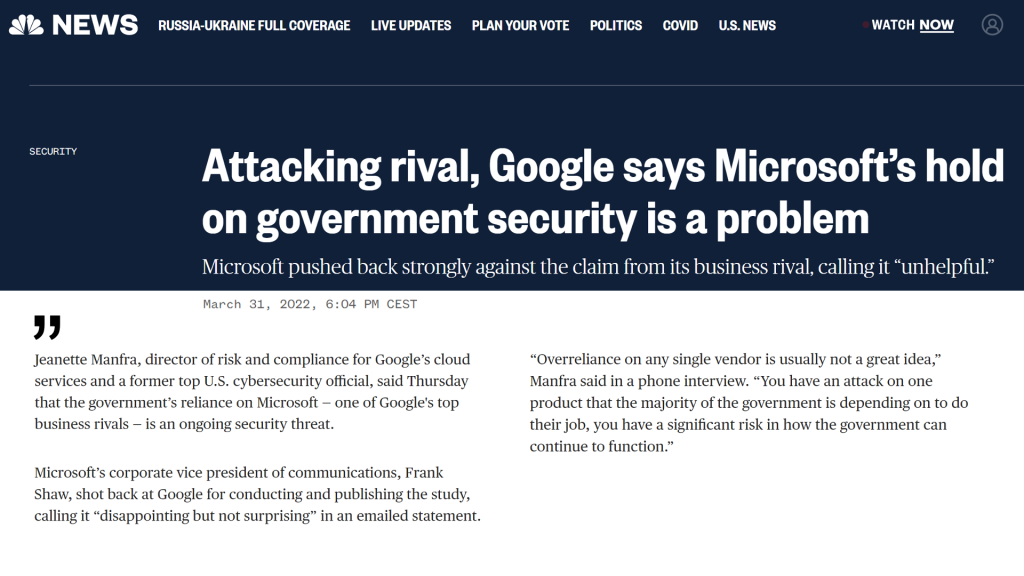
The company in question has also failed to maintain its own internal security, stating in January 2024 that Russian hackers stole internal messages and files from its leadership team, and cybersecurity and legal employees. The intrusion later turned out to be much worse than initially known.
Competitors to the vendor’s security business are also levying sharp criticism, according to a report by GovInfoSecurity:
”Any way you cut it, the threat is very real and very serious, and the prevailing view across the national security community seems to be that [the vendor] is hanging on by a thread,” said Krebs, who served as the first director of the U.S. Cybersecurity and Infrastructure Security Agency. ”These continued incidents pose a significant risk to companies that rely on [the vendor’s] systems and are driving executives in government and industry alike to reevaluate their dependence on [the vendor’s] systems.”
But it’s not just the vendor’s competitors that have raised concerns.
In April 2024, the U.S. Department of Homeland Security published a report outlining ”a cascade of security failures” at the vendor and that ”[the vendor’s] security culture was inadequate”.
”Throughout this review, the Board identified a series of [vendor] operational and strategic decisions that collectively point to a corporate culture that deprioritized both enterprise security investments and rigorous risk management”, the report reads in part.
The board that produced the report consists of government and industry officials, from entities including the Departments of Homeland Security, Justice, and Defense, the NSA, FBI, and others.
Adding to this, BSI, the German Federal Office for Information Security, has asked questions to the same cloud service provider without receiving clear answers back. The issue concerned the provider’s use of so-called double-key encryption (DKE). By using two keys, one of which always remains with the customer, DKE is meant to prevent data leaks in specially secured environments.
However, after the cloud service provider suffered a particularly bad incident, the provider gave BSI information which was so unclear that the BSI couldn’t assess if the attackers were able to access data in plain text anyway. ”Even after repeated requests and threats of legal action, [the provider] did not provide the requested information. Therefore, the BSI is now using the legal instruments at its disposal, explains a BSI spokesperson,” heise Security reports.
Security isn’t easy, but a diversity of views makes it easier
Security isn’t easy. Any solution that becomes large or significant enough will attract adversaries looking for vulnerabilities. We are not raising this issue to point fingers at a single vendor, but to show that an excellent level of security does not necessarily follow automatically from a single company putting a lot of staff resources into security.
With American roots and contributions from around the world, one advantage of OpenStack is that the source code is freely available. Thousands of organisations use OpenStack and thousands of people contribute to its development. This widespread use and participation becomes an advantage by exposing the source code to many eyes and perspectives. If someone wants to perform an independent security review of a certain part of the code, or penetration test a certain implementation, that is entirely possible. For the project, this creates value for all users because it helps to identify and fix security vulnerabilities.
Eggs in the same basket
An organisation can reduce its vulnerability by spreading its eggs into several baskets, instead of putting all of its data in the same cloud that almost everyone else uses. This also reduces vulnerability at the societal level, as one security vulnerability cannot affect large parts of society at the same time.
There is another security perspective to be considered as well: US authorities gain access to the data processed by US cloud service providers. This can be a threat to trade secrets, confidential information and personal privacy. We have written more about the threat of such access in the report What your organisation needs to know about the third adequacy decision.
Deep dependence on a single provider at a national level can even undermine a country’s independence. In Denmark, for example, the association representing regions and municipalities lobbied the government for changes to Danish law to allow Google to use school children’s personal data to improve its cloud services. Some municipalities reported not having a choice but to use Google’s school solutions, while Google wants to use school children’s personal data for these purposes.
One of OpenStack’s advantages is that an organisation does not become dependent on a particular provider. If an organisation assesses that an existing provider of OpenStack-based services doesn’t provide good enough support, doesn’t manage security well enough, or doesn’t maintain competitive prices, it’s perfectly possible to migrate to another provider that provides essentially the same infrastructure service.
This creates an interesting paradox: the easier it is for the customer to leave, the more likely it is that the customer will voluntarily choose to stay. This is because the provider has strong incentives to be responsive to its customers and deliver a secure and reliable service with competitive prices and terms.
Summary regarding US cloud services
- Large resources alone do not guarantee high security. The resources need to be used efficiently and development needs to be done in the right way.
- There are alternatives to US cloud services: Cleura Compliant Cloud, for example.
- Cleura and many other cloud companies sell infrastructure as a service (IaaS) based on OpenStack, one of the world’s most successful open source projects.
- The open source nature of OpenStack provides several advantages from a security point of view:
- development is transparent and hosted by the neutral OpenInfra Foundation. This allows everyone to see that new code is reviewed according to agreed procedures in a secure manner,
- anyone who wants to can perform or commission a security review of the code or penetration test a particular implementation and configuration,
- all else being equal, more eyes on the code makes it more likely that security vulnerabilities will be discovered.
- Since there are many providers of OpenStack-based clouds, both in Sweden and Europe, dissatisfied organisations can switch providers. It isn’t just potentially new customers that get access to beneficial prices and architectural support. Each provider has strong incentives to continuously support existing customers by delivering a quality service with high security at competitive prices. On the other hand, a provider with customers who have difficulty leaving the service is not held accountable to market forces. This increases the likelihood that the supplier raises prices for existing customers and stagnates, including when it comes to security.